Exploring Cloud Application Security
In today's digital age, where information flows seamlessly through the digital realm, ensuring the safety of your data and applications has become more critical than ever. Cloud Application Security stands as a protective shield, guarding your valuable applications and sensitive information from potential threats.
Let's embark on a journey to understand this concept and unravel its significance in the world of technology.
What is Cloud Application Security?
At its core, Cloud Application Security refers to the measures and practices put in place to protect applications that in fact operate in the cloud. Imagine your applications as digital treasures, and Cloud Application Security as the lock and also key that keeps them safe from cyber attackers and potential vulnerabilities. In fact, it involves strategies, tools, and protocols designed to shield your applications from unauthorized access, data breaches, and other digital hazards.
Transitioning from the physical world to the digital one, think of Cloud Application Security as the digital bodyguard that ensures only authorized users can access your applications while keeping malicious entities at bay. In fact, it's like having a vigilant sentry that stands watch over your applications, ensuring they operate smoothly without falling victim to cyber threats.
Do recommend reading about Cloud Security Assessment
The Importance of Cloud Application Security
Now that we've grasped the essence of Cloud Application Security, let's delve into why it holds such paramount importance. Imagine your applications as the heart of your digital operations. In fact, they process, store, and manage your data, enabling your business to function seamlessly. Just as you would protect your heart, it's crucial to safeguard your applications.
As a matter of fact, in today's interconnected world, where cyber threats are constantly evolving, neglecting application security could lead to disastrous consequences. Breaches could result in stolen sensitive data, disrupted operations, and also damaged reputation. This is where Cloud Application Security steps in as your guardian, ensuring that your applications remain resilient and also your data remains confidential.
Cloud Application Security serves as a vital pillar in the realm of technology. It safeguards your applications, enabling them to function smoothly while keeping your sensitive data secure. Just as you wouldn't leave your home unlocked, you shouldn't leave your applications vulnerable. Moreover, with Cloud Application Security in place, you can navigate the digital landscape with confidence, knowing that your applications are protected and your data is safe.
Navigating the world of cloud computing involves comprehending the intricate balance between cloud service providers and customers when it comes to securing cloud environments. Let's delve into these models and uncover how they collaboratively shape a secure digital realm.
As a matter of fact, in this exploration, we'll focus on the three primary cloud application models and their shared responsibilities, illustrating the synergy that underpins cloud security.
1. Infrastructure as a Service (IaaS)
Starting our journey with IaaS, it is a foundation where cloud service providers furnish virtualized computing resources accessible via the internet. In fact, in this model, providers assume the mantle of securing the infrastructure's physical elements, from hardware to networking components and cloud storage systems. On the other hand, customers step into the role of safeguarding the operating systems, applications, and data within this virtual landscape. It's akin to a well-choreographed dance where both partners play a vital role in the overall harmony. Notable providers such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) exemplify this dynamic relationship, often referred to as the Shared Responsibility model.
2. Platform as a Service (PaaS)
Transitioning to PaaS, it is a workshop where customers receive a comprehensive toolbox for developing, testing, and also deploying applications in the cloud. In this scenario, the cloud service provider extends its protective umbrella over both the underlying infrastructure and the platform itself. Customers, in turn, take on the responsibility of securing their unique applications and also data within this sheltered environment. It's like a collaborative orchestra, where the conductor provides the framework, and also individual musicians contribute their skills to create a harmonious symphony. Prominent PaaS providers such as Heroku, Google App Engine, and Microsoft Azure App Service thrive under this security model.
3. Software as a Service (SaaS)
Imagine entering a world where the cloud service provider not only oversees the infrastructure but also delivers fully operational applications accessible through the Internet. In fact, within the SaaS model, the provider's protective umbrella extends over the underlying infrastructure, the platform, and the applications themselves. However, the symphony of security is incomplete without the active participation of customers. In fact, they manage user access, fine-tune security settings, and ensure compliance with regulatory standards. It's like inhabiting a meticulously maintained apartment while also ensuring your personal space remains secure and orderly. Prominent SaaS providers such as Salesforce, Microsoft Office 365, and Google Workspace embody this partnership.
Embracing these cloud application models, organizations and cloud service providers collaborate harmoniously. Also, Explore the Hybrid Cloud Strategy.
The collaboration also facilitated by an array of security tools and features, paves the way for confident deployment, operation, and protection of applications. For instance, F5's Distributed Cloud Services offer a suite of application management, networking, and security solutions. These solutions include robust tools such as web application firewalls, bot defense, and API security, empowering organizations to navigate the cloud landscape with resilience and assurance. In essence, the symbiotic dance of shared responsibilities and advanced security measures ensures a fortified digital future, where cloud application models serve as the pillars of protection.
In the intricate tapestry of cloud computing, mastering cloud application security is like wielding a skilled brush to create a masterpiece of protection.
To achieve this mastery, let's delve into the realm of best practices, the tried-and-true techniques that empower you to fortify your digital creations and keep potential threats at bay.
Cloud Application Security Best Practices: Crafting a Shield of Resilience
Imagine you're a skilled craftsman sculpting a masterpiece. Cloud application security best practices also serve as your toolkit, allowing you to chisel away vulnerabilities and craft a robust shield of resilience.
1. Embrace Robust Authentication and Authorization
Consider authentication and authorization as the foundation of your security fortress. In fact, just as you'd lock the doors to your treasure vault, ensure only authorized users have access to your applications. Multi-factor authentication also adds an extra layer of protection, like requiring multiple keys to open a secure vault.
2. Encrypt Your Data Fortress
In the digital realm, encryption acts as an unbreakable code, rendering your data unreadable to prying eyes. In fact, it's like placing your precious artifacts in an impenetrable vault. Encrypt sensitive information both in transit and at rest to ensure its confidentiality remains intact.
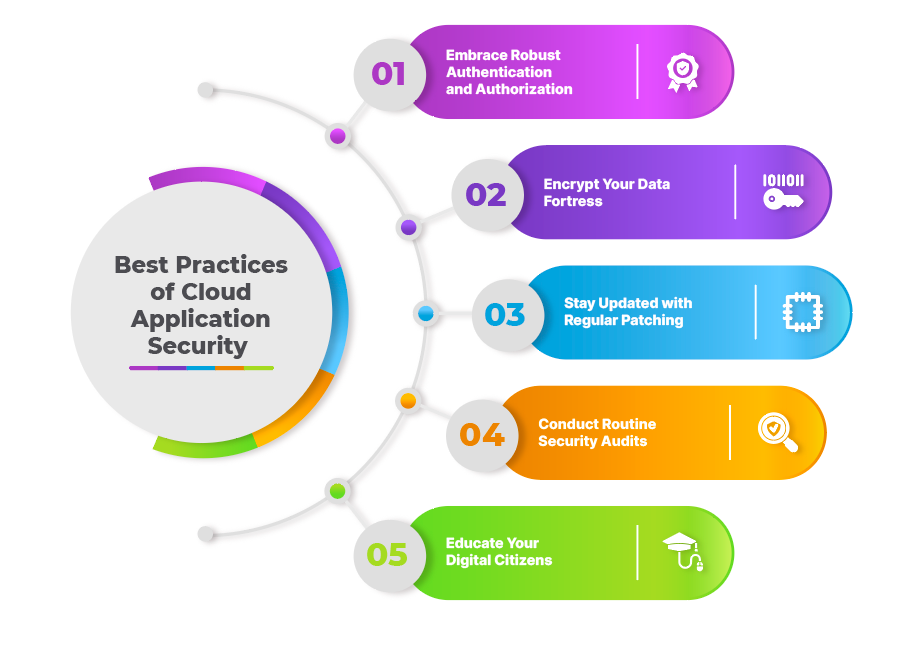
3. Stay Updated with Regular Patching
Think of software vulnerabilities as cracks in your fortress walls. Regular patching acts as a skilled mason, also sealing these cracks and fortifying your defenses. Stay updated with the latest security patches to prevent potential breaches.
4. Conduct Routine Security Audits
Just as an art restorer examines a masterpiece for signs of wear, routine security audits scrutinize your applications for vulnerabilities. These audits identify weak points and enable you to address them before they become exploited.
5. Educate Your Digital Citizens
Imagine your workforce as valuable guardians of your digital realm. Educate them about cybersecurity best practices, empowering them to identify and also report potential threats. In fact, it's like equipping your knights with the knowledge to defend the kingdom.
To proceed with the digital canvas, cloud application security best practices are the strokes that bring your masterpiece to life. In fact, embracing these techniques empowers you to shape a secure and resilient environment, where your applications and data remain shielded from the storms of cyber threats.
Defending Against Security Threats: Unmasking the Challenges and Solutions
In the intricate realm of cloud application security, identifying and addressing security threats is akin to shining a light on potential hazards and also arming yourself with effective defense mechanisms. Let's embark on a journey to unravel these threats and explore strategies to counteract them, ensuring the safety of your digital haven.
Identifying and Addressing Security Threats: Illuminating the Shadows
In a cloud environment as a bustling cityscape, with information flowing like pedestrians along digital streets, in fact, in this bustling ecosystem, threats can lurk in the shadows, seeking to exploit vulnerabilities and compromise your valuable data. Identifying these threats is akin to having vigilant sentinels stationed throughout the city, alert to any unusual activities.
Common threats include cyberattacks like malware, phishing, and denial-of-service attacks. Think of these threats as digital adversaries that attempt to breach your defenses. By recognizing their tactics and understanding their motives, you equip yourself with the knowledge needed to detect and respond effectively.
In the vast sea of technological options. Choosing the right cloud application security solution is akin to charting a course through uncharted waters. Let's embark on a journey to understand the art of evaluating and also selecting security tools. Moreover, that will fortify your digital landscape against potential threats.
Selecting the Right Security Solution: Your Digital Compass
Imagine you're an explorer on a quest for treasure, equipped with a trusty compass. Choosing the right security solution serves as your digital compass. In fact, it guides you through a plethora of options and helps you navigate toward a secure haven.
1. Identify Your Needs and Objectives
Just as an explorer sets a clear goal, identify your security needs and objectives. Understand what you aim to achieve with your security solution. Whether it's protecting sensitive data, mitigating specific risks, or ensuring compliance with industry standards.
2. Assess the Threat Landscape
Think of your assessment as an exploration of the terrain. Evaluate your digital environment to identify potential threats and vulnerabilities. This assessment is like studying the topography to understand where potential dangers may lurk.
Check more details with Cloud Security Assessment – A Comprehensive Guide to Elevate Your Cloud Security
3. Explore Available Security Tools
Imagine your journey through a marketplace filled with diverse tools and resources. In fact, explore available security tools and solutions, each offering unique features and capabilities. It's like browsing a marketplace to find the best tools for your expedition.
4. Consider Integration and Compatibility
In the digital realm, compatibility is key. In fact, consider how the selected security tools integrate with your existing applications and systems. It's like ensuring that your equipment works seamlessly together for a successful expedition.
5. Evaluate User-Friendliness and Support
Just as explorers rely on their gear, ensure your chosen security solution is user-friendly and also well-supported. In fact, consider the ease of implementation, user interface, and available support services. It's like selecting gear that is easy to use and backed by a reliable support team.
Transitioning from the explorer's journey to the digital landscape, selecting the right security solution is your compass for a secure cloud environment. Just as a skilled explorer carefully selects the tools that best suit their expedition, in fact, making informed choices empowers you to fortify your applications against potential threats.
Conclusion
Emorphis Technologies can play a pivotal role in enhancing your cloud application security through its expertise and also comprehensive services. Here's how Emorphis can help:
- Expert Guidance - Emorphis boasts a team of seasoned experts in cloud application security. In fact, we can provide you with valuable insights, best practices, and tailored recommendations to fortify your applications against potential threats. Check our Cloud Advisory Services.
- Customized Solutions - Emorphis can analyze your unique business requirements and design customized cloud application security solutions. In fact, these solutions address your specific challenges and align with your organization's goals.
- Risk Assessment and Mitigation - Emorphis can also conduct thorough risk assessments of your cloud applications, identifying vulnerabilities and potential security gaps. Subsequently, they can develop strategies to mitigate these risks effectively.
- Secure Development Practices - Emorphis can guide you in implementing secure coding practices, also ensuring that your applications are built with security in mind from the ground up. This helps prevent vulnerabilities in the development process.
- Third-Party Integration Security - Emorphis can assist in securing third-party integrations and APIs within your cloud applications. By implementing robust authentication, authorization, and encryption mechanisms, in fact, they can safeguard these crucial connections.
Click the link to look for more details on Cloud Operations Management Services.
Some more...
Emorphis Technologies can be your partner in building a fortified cloud application security framework. How, check the following points.
- Incident Response Planning - Emorphis can help you establish robust incident response protocols, also ensuring that you are well-prepared to detect, respond to, and recover from security incidents swiftly and effectively.
- Continuous Monitoring - Emorphis can set up continuous monitoring mechanisms that keep a vigilant eye on your cloud applications for any signs of unauthorized access, also unusual activities, or potential breaches. Check our details on Cloud Native App Development Services.
- Compliance and Regulations - Emorphis can guide you in aligning your cloud application security practices with relevant compliance standards and regulations, also ensuring that your applications meet legal requirements.
- Cutting-Edge Tools and Technologies - Emorphis leverages the latest cloud security tools and technologies also to provide you with state-of-the-art solutions. In fact, this includes intrusion detection systems, firewalls, encryption protocols, and more.
- Education and Training - Emorphis can organize training sessions and workshops for your team, also empowering them with the knowledge and skills needed to implement and maintain robust cloud application security practices.
With our expertise, tailored solutions, and also dedication to staying at the forefront of cloud security trends, we can empower your organization to navigate the complex landscape of cloud application security with confidence and resilience.
FAQ's
1. What is cloud application security, and why is it important?
Cloud application security involves protecting applications and data hosted in the cloud from unauthorized access, data breaches, and other threats. In fact, it's crucial to ensure the confidentiality, integrity, and availability of sensitive information and maintain operational stability.
2. What is the difference between cloud security and cloud application security?
Cloud security focuses on securing overall cloud environments, including networks and infrastructure, while cloud application security specifically addresses the protection of applications, their data, and also interactions within the cloud.
3. What are the different cloud application models, and how do they impact security?
Cloud application models - SaaS, PaaS, and IaaS - determine the level of control and responsibilities shared between the cloud provider and the user. In fact, these models impact security by influencing who is responsible for securing different layers of the application stack.
4. What are the common security threats faced by cloud applications?
Common threats include data breaches, unauthorized access, DDoS attacks, insecure APIs, and also misconfigured cloud settings. These threats can compromise sensitive data and also disrupt application functionality.
5. What best practices should I follow to enhance cloud application security?
Implement encryption, strong authentication, access controls, regular patching, secure coding practices, and continuous monitoring to strengthen your cloud application security.
6. How can I formulate an effective cloud application security strategy?
Craft a strategy by identifying your security objectives, assessing risks, selecting appropriate security measures, implementing access controls, and establishing incident response protocols.
7. What criteria should I consider when selecting a cloud application security solution?
Evaluate tools based on their effectiveness in intrusion detection, firewall protection, vulnerability scanning, compatibility, ease of integration, and reliable support.
8. How does cloud application security align with compliance standards and regulations?
Cloud application security practices often align with industry-specific regulations, data protection laws, and compliance frameworks to ensure data privacy and legal adherence.
9. What steps can I take to secure third-party integrations and APIs within my cloud applications?
Employ authentication, authorization mechanisms, and encryption for third-party integrations and APIs. Regularly audit and monitor these connections for potential vulnerabilities.
Yes, under the shared responsibility model, both your organization and the cloud provider have distinct security responsibilities. While the provider secures the infrastructure, you're responsible for securing your applications and data within the cloud environment.








One Reply to “Cloud Application Security – Safeguarding Your Digital Frontier”
Comments are closed.